-->
Important
Windows 10 in S mode is designed for security and performance, exclusively running apps from the Microsoft Store. If you want to install an app that isn't available in the Microsoft Store, you'll need to switch out of S mode. Switching out of S mode is one-way. If you make the switch, you won't be able to go back to Windows 10 in S mode. Mazenet Technologies is a comprehensive IT service provider of enterprise security solutions, offering a full range of Networking to support business infrastructure. Our 18+ years of expertise in storage optimization, cloud migration, and managed security services have aided the timely delivery of solutions by enhancing operational excellence.
The Windows Licensing Monitoring Service is a Win32 program that can be started by the Service Controller and that obeys the service control protocol. In Windows 8 it is starting automatically during the operating system startup. Upgrade path: 2008 - 2008 R2 (using Eval ISO) - 2012 R2 (using retail disk) I currently have Windows 2012 R2 installed. I've upgraded the 2008 to 2008 R2 using a eval iso from Microsoft.
Welcome to Microsoft Defender for Endpoint, the new name for Microsoft Defender Advanced Threat Protection. Read more about this and other updates here. We'll be updating names in products and in the docs in the near future.
Applies to:
- Windows Server 2008 R2 SP1
- Windows Server 2012 R2
- Windows Server 2016
- Windows Server (SAC) version 1803 and later
- Windows Server 2019 and later
- Windows Server 2019 core edition
Want to experience Defender for Endpoint? Sign up for a free trial.
Defender for Endpoint extends support to also include the Windows Server operating system. This support provides advanced attack detection and investigation capabilities seamlessly through the Microsoft Defender Security Center console.
For a practical guidance on what needs to be in place for licensing and infrastructure, see Protecting Windows Servers with Defender for Endpoint.
For guidance on how to download and use Windows Security Baselines for Windows servers, see Windows Security Baselines.
Windows Server 2008 R2 SP1, Windows Server 2012 R2, and Windows Server 2016
You can onboard Windows Server 2008 R2 SP1, Windows Server 2012 R2, and Windows Server 2016 to Defender for Endpoint by using any of the following options:
- Option 1: Onboard by installing and configuring Microsoft Monitoring Agent (MMA)
- Option 2: Onboard through Azure Security Center
- Option 3: Onboard through Microsoft Endpoint Configuration Manager version 2002 and later
After completing the onboarding steps using any of the provided options, you'll need to Configure and update System Center Endpoint Protection clients.
Note
Defender for Endpoint standalone server license is required, per node, in order to onboard a Windows server through Microsoft Defender Security Center (Option 1), or an Azure Security Center Standard license is required, per node, in order to onboard a Windows server through Azure Security Center (Option 2), see Supported features available in Azure Security Center.
Option 1: Onboard by installing and configuring Microsoft Monitoring Agent (MMA)
You'll need to install and configure MMA for Windows servers to report sensor data to Defender for Endpoint. For more information, see Collect log data with Azure Log Analytics agent.
If you're already leveraging System Center Operations Manager (SCOM) or Azure Monitor (formerly known as Operations Management Suite (OMS)), attach the Microsoft Monitoring Agent (MMA) to report to your Defender for Endpoint workspace through Multihoming support.
In general, you'll need to take the following steps:
- Fulfill the onboarding requirements outlined in Before you begin section.
- Turn on server monitoring from Microsoft Defender Security center.
- Install and configure MMA for the server to report sensor data to Defender for Endpoint.
- Configure and update System Center Endpoint Protection clients.
Tip
After onboarding the device, you can choose to run a detection test to verify that it is properly onboarded to the service. For more information, see Run a detection test on a newly onboarded Defender for Endpoint endpoint.
Before you begin
Perform the following steps to fulfill the onboarding requirements:
For Windows Server 2008 R2 SP1 or Windows Server 2012 R2, ensure that you install the following hotfix:
In addition, for Windows Server 2008 R2 SP1, ensure that you fulfill the following requirements:
- Install the February monthly update rollup
- Install either .NET framework 4.5 (or later) or KB3154518
For Windows Server 2008 R2 SP1 and Windows Server 2012 R2: Configure and update System Center Endpoint Protection clients.
Note
This step is required only if your organization uses System Center Endpoint Protection (SCEP) and you're onboarding Windows Server 2008 R2 SP1 and Windows Server 2012 R2.
Install and configure Microsoft Monitoring Agent (MMA) to report sensor data to Microsoft Defender for Endpoint
Download the agent setup file: Windows 64-bit agent.
Using the Workspace ID and Workspace key obtained in the previous procedure, choose any of the following installation methods to install the agent on the Windows server:
- Manually install the agent using setup
On the Agent Setup Options page, choose Connect the agent to Azure Log Analytics (OMS). - Install the agent using the command line and configure the agent using a script.
- Manually install the agent using setup
Configure Windows server proxy and Internet connectivity settings if needed
If your servers need to use a proxy to communicate with Defender for Endpoint, use one of the following methods to configure the MMA to use the proxy server:
If a proxy or firewall is in use, please ensure that servers can access all of the Microsoft Defender ATP service URLs directly and without SSL interception. For more information, see enable access to Defender for Endpoint service URLs. Use of SSL interception will prevent the system from communicating with the Defender for Endpoint service.
Once completed, you should see onboarded Windows servers in the portal within an hour.
Option 2: Onboard Windows servers through Azure Security Center
In the Microsoft Defender Security Center navigation pane, select Settings > Device management > Onboarding.
Select Windows Server 2008 R2 SP1, 2012 R2 and 2016 as the operating system.
Click Onboard Servers in Azure Security Center.
Follow the onboarding instructions in Microsoft Defender for Endpoint with Azure Security Center.
After completing the onboarding steps, you'll need to Configure and update System Center Endpoint Protection clients.
Note
- For onboarding via Azure Defender for Servers (previously Azure Security Center Standard Edition) to work as expected, the server must have an appropriate workspace and key configured within the Microsoft Monitoring Agent (MMA) settings.
- Once configured, the appropriate cloud management pack is deployed on the machine and the sensor process (MsSenseS.exe) will be deployed and started.
- This is also required if the server is configured to use an OMS Gateway server as proxy.
Option 3: Onboard Windows servers through Microsoft Endpoint Configuration Manager version 2002 and later
You can onboard Windows Server 2012 R2 and Windows Server 2016 by using Microsoft Endpoint Configuration Manager version 2002 and later. For more information, see Microsoft Defender for Endpointin Microsoft Endpoint Configuration Manager current branch.
Disable Windows Service Gpo
After completing the onboarding steps, you'll need to Configure and update System Center Endpoint Protection clients.
Windows Server (SAC) version 1803, Windows Server 2019, and Windows Server 2019 Core edition
You can onboard Windows Server (SAC) version 1803, Windows Server 2019, or Windows Server 2019 Core edition by using the following deployment methods:
Note
- The Onboarding package for Windows Server 2019 through Microsoft Endpoint Configuration Manager currently ships a script. For more information on how to deploy scripts in Configuration Manager, see Packages and programs in Configuration Manager.
- A local script is suitable for a proof of concept but should not be used for production deployment. For a production deployment, we recommend using Group Policy, Microsoft Endpoint Configuration Manager, or Intune.
Support for Windows Server provides deeper insight into server activities, coverage for kernel and memory attack detection, and enables response actions.
Configure Defender for Endpoint onboarding settings on the Windows server. For more information, see Onboard Windows 10 devices.
If you're running a third-party antimalware solution, you'll need to apply the following Microsoft Defender AV passive mode settings. Verify that it was configured correctly:
Set the following registry entry:
- Path:
HKLMSOFTWAREPoliciesMicrosoftWindows Advanced Threat Protection - Name: ForceDefenderPassiveMode
- Type: REG_DWORD
- Value: 1
- Path:
Run the following PowerShell command to verify that the passive mode was configured:
Confirm that a recent event containing the passive mode event is found:
Run the following command to check if Microsoft Defender AV is installed:
sc.exe query WindefendIf the result is 'The specified service does not exist as an installed service', then you'll need to install Microsoft Defender AV. For more information, see Microsoft Defender Antivirus in Windows 10.
For information on how to use Group Policy to configure and manage Microsoft Defender Antivirus on your Windows servers, see Use Group Policy settings to configure and manage Microsoft Defender Antivirus.
Integration with Azure Security Center
Defender for Endpoint can integrate with Azure Security Center to provide a comprehensive Windows server protection solution. With this integration, Azure Security Center can leverage the power of Defender for Endpoint to provide improved threat detection for Windows Servers.
The following capabilities are included in this integration:
Automated onboarding - Defender for Endpoint sensor is automatically enabled on Windows Servers that are onboarded to Azure Security Center. For more information on Azure Security Center onboarding, see Onboarding to Azure Security Center Standard for enhanced security.
Note
Automated onboarding is only applicable for Windows Server 2008 R2 SP1, Windows Server 2012 R2, and Windows Server 2016.
Windows servers monitored by Azure Security Center will also be available in Defender for Endpoint - Azure Security Center seamlessly connects to the Defender for Endpoint tenant, providing a single view across clients and servers. In addition, Defender for Endpoint alerts will be available in the Azure Security Center console.
Server investigation - Azure Security Center customers can access Microsoft Defender Security Center to perform detailed investigation to uncover the scope of a potential breach.
Important
- When you use Azure Security Center to monitor servers, a Defender for Endpoint tenant is automatically created (in the US for US users, in the EU for European and UK users).
Data collected by Defender for Endpoint is stored in the geo-location of the tenant as identified during provisioning. - If you use Defender for Endpoint before using Azure Security Center, your data will be stored in the location you specified when you created your tenant even if you integrate with Azure Security Center at a later time.
- Once configured, you cannot change the location where your data is stored. If you need to move your data to another location, you need to contact Microsoft Support to reset the tenant.
Server endpoint monitoring utilizing this integration has been disabled for Office 365 GCC customers.
Configure and update System Center Endpoint Protection clients
Defender for Endpoint integrates with System Center Endpoint Protection. The integration provides visibility to malware detections and to stop propagation of an attack in your organization by banning potentially malicious files or suspected malware.
The following steps are required to enable this integration:
Install the January 2017 anti-malware platform update for Endpoint Protection clients.
Configure the SCEP client Cloud Protection Service membership to the Advanced setting.
Offboard Windows servers
You can offboard Windows Server (SAC), Windows Server 2019, and Windows Server 2019 Core edition in the same method available for Windows 10 client devices.
For other Windows server versions, you have two options to offboard Windows servers from the service:
- Uninstall the MMA agent
- Remove the Defender for Endpoint workspace configuration
Note
Offboarding causes the Windows server to stop sending sensor data to the portal but data from the Windows server, including reference to any alerts it has had will be retained for up to 6 months.
Uninstall Windows servers by uninstalling the MMA agent
To offboard the Windows server, you can uninstall the MMA agent from the Windows server or detach it from reporting to your Defender for Endpoint workspace. After offboarding the agent, the Windows server will no longer send sensor data to Defender for Endpoint.For more information, see To disable an agent.
Remove the Defender for Endpoint workspace configuration
To offboard the Windows server, you can use either of the following methods:
- Remove the Defender for Endpoint workspace configuration from the MMA agent
- Run a PowerShell command to remove the configuration
Remove the Defender for Endpoint workspace configuration from the MMA agent
In the Microsoft Monitoring Agent Properties, select the Azure Log Analytics (OMS) tab.
Select the Defender for Endpoint workspace, and click Remove.
Run a PowerShell command to remove the configuration
Get your Workspace ID:
In the navigation pane, select Settings > Onboarding.
Select Windows Server 2008 R2 SP1, 2012 R2 and 2016 as the operating system and get your Workspace ID:
Open an elevated PowerShell and run the following command. Use the Workspace ID you obtained and replacing
WorkspaceID:
Related topics
got a new acer laptop with win 8.1 - seems to have a large number of services running. Download x7 macro.
can't tell which are needed and which are just bloat-ware.
any idea which ones i can disable?
Windows Licensing Monitoring Service (WLMS). If Windows Licensing Monitoring Service fails to load. If you remove or disable the WLMS service, Windows 7 won't.
Disable Windows License Monitoring Service
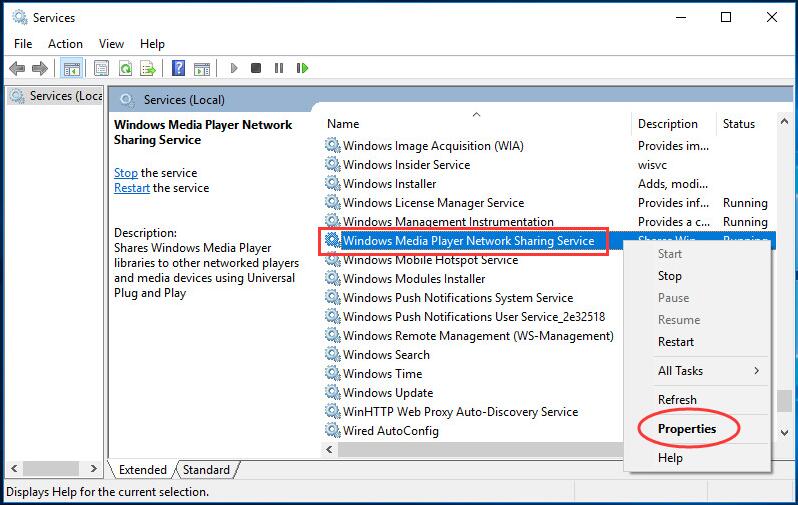
Name PID Description Status Group
WSearch 3408 Windows Search Running
WMPNetworkSvc Windows Media Player Network Sharing Service Stopped
wmiApSrv WMI Performance Adapter Stopped
WinDefend Windows Defender Service Stopped
WdNisSvc Windows Defender Network Inspection Service Stopped
wbengine Block Level Backup Engine Service Stopped
VSS Volume Shadow Copy Stopped
vds Virtual Disk Stopped
VaultSvc Credential Manager Stopped
UI0Detect Interactive Services Detection Stopped
UEIPSvc 4388 User Experience Improvement Program Running
TrustedInstaller Windows Modules Installer Stopped
sppsvc Software Protection Stopped
Spooler 1424 Print Spooler Running
SNMPTRAP SNMP Trap Stopped
SamSs 744 Security Accounts Manager Running
RpcLocator Remote Procedure Call (RPC) Locator Stopped
RMSvc 4568 Quick Access RadioMgr Service Running
RichVideo 1624 Cyberlink RichVideo Service(CRVS) Running
QASvc 3760 Quick Access Service Running
PerfHost Performance Counter DLL Host Stopped
NetTcpPortSharing Net.Tcp Port Sharing Service Stopped
Netlogon Netlogon Stopped
msiserver Windows Installer Stopped
MSDTC Distributed Transaction Coordinator Stopped
LMSvc 2040 Launch Manager Service Running
KeyIso CNG Key Isolation Stopped
Intel(R) Capability Licensing Service TCP IP Interface Intel(R) Capability Licensing Service TCP IP Interface Stopped
Intel(R) Capability Licensing Service Interface 2012 Intel(R) Capability Licensing Service Interface Running
igfxCUIService1.0.0.0 656 Intel(R) HD Graphics Control Panel Service Running
IEEtwCollectorService Internet Explorer ETW Collector Service Stopped
ICCS Intel(R) Integrated Clock Controller Service - Intel(R) ICCS Stopped
GamesAppService GamesAppService Stopped
GamesAppIntegrationService 4876 GamesAppIntegrationService Running
FontCache3.0.0.0 3152 Windows Presentation Foundation Font Cache 3.0.0.0 Running
Fax Fax Stopped
ePowerSvc 4500 ePower Service Running
EFS Encrypting File System (EFS) Stopped
cphs Intel(R) Content Protection HECI Service Stopped
COMSysApp COM+ System Application Stopped
CCDMonitorService 1616 CCDMonitorService Running
avast! Antivirus 1240 avast! Alesis quadraverb patch editor. Antivirus Running
AtherosSvc 1592 AtherosSvc Running
ALG Application Layer Gateway Service Stopped
AppReadiness App Readiness Stopped AppReadiness
AxInstSV ActiveX Installer (AxInstSV) Stopped AxInstSVGroup
SystemEventsBroker 816 System Events Broker Running DcomLaunch
Power 816 Power Running DcomLaunch
PlugPlay 816 Plug and Play Running DcomLaunch
LSM 816 Local Session Manager Running DcomLaunch
DeviceInstall Device Install Service Stopped DcomLaunch
DcomLaunch 816 DCOM Server Process Launcher Running DcomLaunch
BrokerInfrastructure 816 Background Tasks Infrastructure Service Running DcomLaunch
defragsvc Optimize drives Stopped defragsvc
vmicrdv Hyper-V Remote Desktop Virtualization Service Stopped ICService
vmicheartbeat Hyper-V Heartbeat Service Stopped ICService
stisvc Windows Image Acquisition (WIA) Stopped imgsvc
workfolderssvc Work Folders Stopped LocalService
WinHttpAutoProxySvc 440 WinHTTP Web Proxy Auto-Discovery Service Running LocalService
WebClient WebClient Stopped LocalService
WdiServiceHost 440 Diagnostic Service Host Running LocalService
W32Time Windows Time Stopped LocalService
THREADORDER Thread Ordering Server Stopped LocalService
SstpSvc Secure Socket Tunneling Protocol Service Stopped LocalService
RemoteRegistry Remote Registry Stopped localService
nsi 440 Network Store Interface Service Running LocalService
netprofm 440 Network List Service Running LocalService
lltdsvc Link-Layer Topology Discovery Mapper Stopped LocalService
FontCache 440 Windows Font Cache Service Running LocalService
fdPHost 440 Function Discovery Provider Host Running LocalService
EventSystem 440 COM+ Event System Running LocalService
bthserv Bluetooth Support Service Stopped LocalService
wcncsvc 2380 Windows Connect Now - Config Registrar Running LocalServiceAndNoImpersonation
upnphost 2380 UPnP Device Host Running LocalServiceAndNoImpersonation
TimeBroker 2380 Time Broker Running LocalServiceAndNoImpersonation
SSDPSRV 2380 SSDP Discovery Running LocalServiceAndNoImpersonation
SensrSvc Sensor Monitoring Service Stopped LocalServiceAndNoImpersonation
SCardSvr Smart Card Stopped LocalServiceAndNoImpersonation
QWAVE Quality Windows Audio Video Experience Stopped LocalServiceAndNoImpersonation
FDResPub 2380 Function Discovery Resource Publication Running LocalServiceAndNoImpersonation
wscsvc 1008 Security Center Running LocalServiceNetworkRestricted
WPCSvc Family Safety Stopped LocalServiceNetworkRestricted
Wcmsvc 1008 Windows Connection Manager Running LocalServiceNetworkRestricted
vmictimesync Hyper-V Time Synchronization Service Stopped LocalServiceNetworkRestricted
lmhosts 1008 TCP/IP NetBIOS Helper Running LocalServiceNetworkRestricted
HomeGroupProvider 1008 HomeGroup Provider Running LocalServiceNetworkRestricted
EventLog 1008 Windows Event Log Running LocalServiceNetworkRestricted
Dhcp 1008 DHCP Client Running LocalServiceNetworkRestricted
Audiosrv 1008 Windows Audio Running LocalServiceNetworkRestricted
AppIDSvc Application Identity Stopped LocalServiceNetworkRestricted
WwanSvc WWAN AutoConfig Stopped LocalServiceNoNetwork
pla Performance Logs & Alerts Stopped LocalServiceNoNetwork
NcdAutoSetup 1468 Network Connected Devices Auto-Setup Running LocalServiceNoNetwork
MpsSvc 1468 Windows Firewall Running LocalServiceNoNetwork
DPS 1468 Diagnostic Policy Service Running LocalServiceNoNetwork
BFE 1468 Base Filtering Engine Running LocalServiceNoNetwork
PNRPsvc Peer Name Resolution Protocol Stopped LocalServicePeerNet
PNRPAutoReg PNRP Machine Name Publication Service Stopped LocalServicePeerNet
p2psvc Peer Networking Grouping Stopped LocalServicePeerNet
p2pimsvc Peer Networking Identity Manager Stopped LocalServicePeerNet
wudfsvc Windows Driver Foundation - User-mode Driver Framework Stopped LocalSystemNetworkRestricted
WPDBusEnum Portable Device Enumerator Service Stopped LocalSystemNetworkRestricted
WlanSvc 944 WLAN AutoConfig Running LocalSystemNetworkRestricted
WiaRpc Still Image Acquisition Events Stopped LocalSystemNetworkRestricted
WdiSystemHost Diagnostic System Host Stopped LocalSystemNetworkRestricted
vmicvss Hyper-V Volume Shadow Copy Requestor Stopped LocalSystemNetworkRestricted
vmicshutdown Hyper-V Guest Shutdown Service Stopped LocalSystemNetworkRestricted
vmickvpexchange Hyper-V Data Exchange Service Stopped LocalSystemNetworkRestricted
vmicguestinterface Hyper-V Guest Service Interface Stopped LocalSystemNetworkRestricted
UmRdpService Remote Desktop Services UserMode Port Redirector Stopped LocalSystemNetworkRestricted
TrkWks 944 Distributed Link Tracking Client Running LocalSystemNetworkRestricted
TabletInputService Touch Keyboard and Handwriting Panel Service Stopped LocalSystemNetworkRestricted
SysMain 944 Superfetch Running LocalSystemNetworkRestricted
svsvc Spot Verifier Stopped LocalSystemNetworkRestricted
StorSvc Storage Service Stopped LocalSystemNetworkRestricted
ScDeviceEnum Smart Card Device Enumeration Service Stopped LocalSystemNetworkRestricted
PcaSvc 944 Program Compatibility Assistant Service Running LocalSystemNetworkRestricted
Netman 944 Network Connections Running LocalSystemNetworkRestricted
NcbService 944 Network Connection Broker Running LocalSystemNetworkRestricted
HomeGroupListener HomeGroup Listener Stopped LocalSystemNetworkRestricted
hidserv Human Interface Device Service Stopped LocalSystemNetworkRestricted
fhsvc File History Service Stopped LocalSystemNetworkRestricted
dot3svc Wired AutoConfig Stopped LocalSystemNetworkRestricted
DeviceAssociationService 944 Device Association Service Running LocalSystemNetworkRestricted
AudioEndpointBuilder 944 Windows Audio Endpoint Builder Running LocalSystemNetworkRestricted
wuauserv Windows Update Stopped netsvcs
wlidsvc Microsoft Account Sign-in Assistant Stopped netsvcs
Winmgmt 328 Windows Management Instrumentation Running netsvcs
wercplsupport Problem Reports and Solutions Control Panel Support Stopped netsvcs
Themes 328 Themes Running netsvcs
ShellHWDetection 328 Shell Hardware Detection Running netsvcs
SharedAccess Internet Connection Sharing (ICS) Stopped netsvcs
SessionEnv Remote Desktop Configuration Stopped netsvcs
SENS 328 System Event Notification Service Running netsvcs
seclogon Secondary Logon Stopped netsvcs
SCPolicySvc Smart Card Removal Policy Stopped netsvcs
Schedule 328 Task Scheduler Running netsvcs
RemoteAccess Routing and Remote Access Stopped netsvcs
RasMan Remote Access Connection Manager Stopped netsvcs
RasAuto Remote Access Auto Connection Manager Stopped netsvcs
ProfSvc 328 User Profile Service Running netsvcs
NcaSvc Network Connectivity Assistant Stopped NetSvcs
MSiSCSI Microsoft iSCSI Initiator Service Stopped netsvcs
MMCSS Multimedia Class Scheduler Stopped netsvcs
lfsvc Windows Location Framework Service Stopped netsvcs
LanmanServer 328 Server Running netsvcs
iphlpsvc 328 IP Helper Running NetSvcs
IKEEXT 328 IKE and AuthIP IPsec Keying Modules Running netsvcs
hkmsvc Health Key and Certificate Management Stopped netsvcs
gpsvc Group Policy Client Stopped netsvcs
Eaphost Extensible Authentication Protocol Stopped netsvcs
DsmSvc Device Setup Manager Stopped netsvcs
CertPropSvc Certificate Propagation Stopped netsvcs
Browser 328 Computer Browser Running netsvcs
BITS 328 Background Intelligent Transfer Service Running netsvcs
BDESVC BitLocker Drive Encryption Service Stopped netsvcs
Appinfo 328 Application Information Running netsvcs
AeLookupSvc Application Experience Stopped netsvcs
WinRM Windows Remote Management (WS-Management) Stopped NetworkService
Wecsvc Windows Event Collector Stopped NetworkService
TermService Remote Desktop Services Stopped NetworkService
TapiSrv Telephony Stopped NetworkService
NlaSvc 1148 Network Location Awareness Running NetworkService
napagent Network Access Protection Agent Stopped NetworkService
LanmanWorkstation 1148 Workstation Running NetworkService
Dnscache 1148 DNS Client Running NetworkService
CryptSvc 1148 Cryptographic Services Running NetworkService
KtmRm KtmRm for Distributed Transaction Coordinator Stopped NetworkServiceAndNoImpersonation
PolicyAgent IPsec Policy Agent Stopped NetworkServiceNetworkRestricted
PrintNotify Printer Extensions and Notifications Stopped print
RpcSs 860 Remote Procedure Call (RPC) Running rpcss
RpcEptMapper 860 RPC Endpoint Mapper Running RPCSS
smphost Microsoft Storage Spaces SMP Stopped smphost
swprv Microsoft Software Shadow Copy Provider Stopped swprv
WbioSrvc Windows Biometric Service Stopped WbioSvcGroup
WcsPlugInService Windows Color System Stopped wcssvc
WEPHOSTSVC Windows Encryption Provider Host Service Stopped WepHostSvcGroup
WerSvc Windows Error Reporting Service Stopped WerSvcGroup
WSService Windows Store Service (WSService) Stopped wsappx
AppXSvc AppX Deployment Service (AppXSVC) Stopped wsappx
Disable Services Windows 10
Windows Licensing Monitoring Service - Windows 7 Service
This service monitors the Windows software license state.
This service also exists in Windows 10 and 8.
Startup Type
| Windows 7 edition | without SP | SP1 |
|---|---|---|
| Starter | not exists | not exists |
| Home Basic | not exists | not exists |
| Home Premium | not exists | not exists |
| Professional | not exists | not exists |
| Ultimate | not exists | not exists |
| Enterprise | Automatic | Automatic |
Default Properties
| Display name: | Windows Licensing Monitoring Service |
| Service name: | WLMS |
| Type: | own |
| Path: | %WinDir%system32wlmswlms.exe |
| Error control: | critical |
| Object: | LocalSystem |
Default Behavior
Software Licensing Service Windows
The Windows Licensing Monitoring Service runs as LocalSystem in its own process. It does not share an executable file with other services. If the Windows Licensing Monitoring Service fails to load or initialize, the error is logged and the computer attempts to restart with the LastKnownGood configuration. If the LastKnownGood configuration fails, Windows 7 startup also fails, and the boot process halts with a Stop error. If you disable this service, Windows 7 will fail to start. Do NOT change this service startup configuration if your computer is working.
Dependencies
Windows Licensing Monitoring Service will not start, if the Software Protection service is stopped or disabled.
Restore Default Startup Type for Windows Licensing Monitoring Service
Automated Restore
1. Select your Windows 7 edition and Service Pack, and then click on the Download button below.
2. Save the RestoreWindowsLicensingMonitoringServiceWindows7.bat file to any folder on your hard drive.
3. Right-click the downloaded batch file and select Run as administrator.
4. Restart the computer to save changes.
Disable Services Windows 10
Note. Make sure that the wlms.exe file exists in the %WinDir%system32wlms folder. If this file is missing you can try to restore it from your Windows 7 installation media.